💜 We're always looking to improve your experience.
-
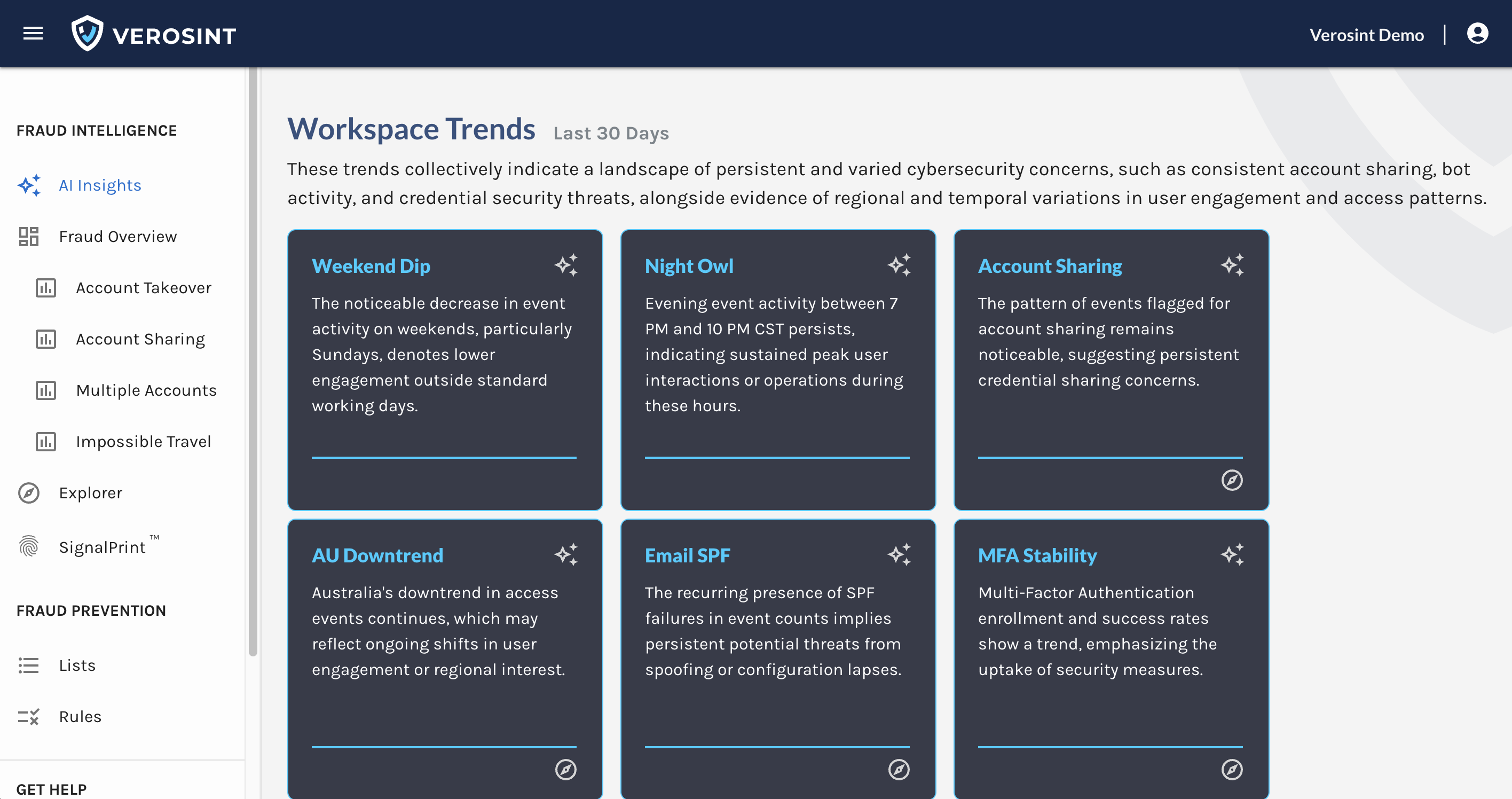
We updated the look and feel of AI Insights, so that it's easier for you to digest a lot of info quickly and discern which insights you might care to dig deeper into.
The biggest change is that we added Insight Types to the AI Insights page, so you can quickly filter (out) the insights you care about.
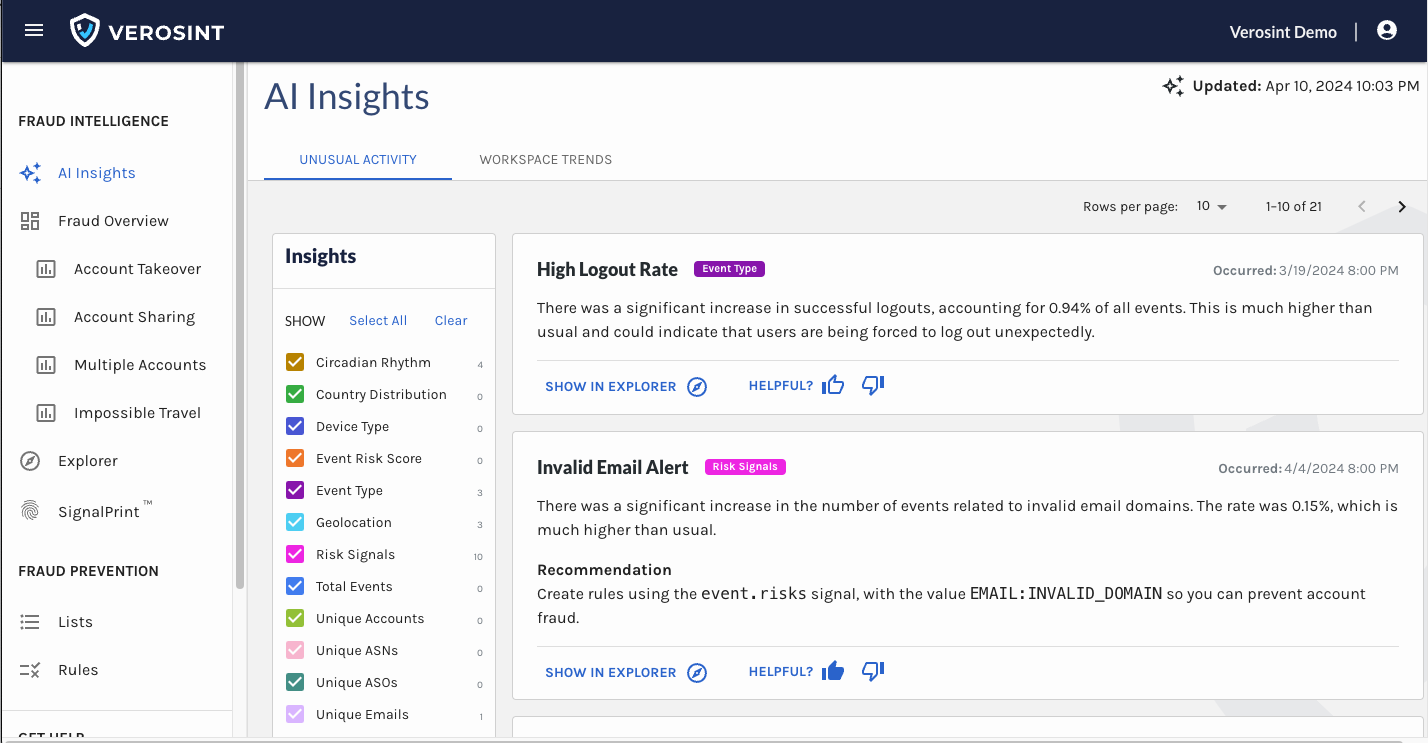
Check out the new look and feel of AI Insights
-
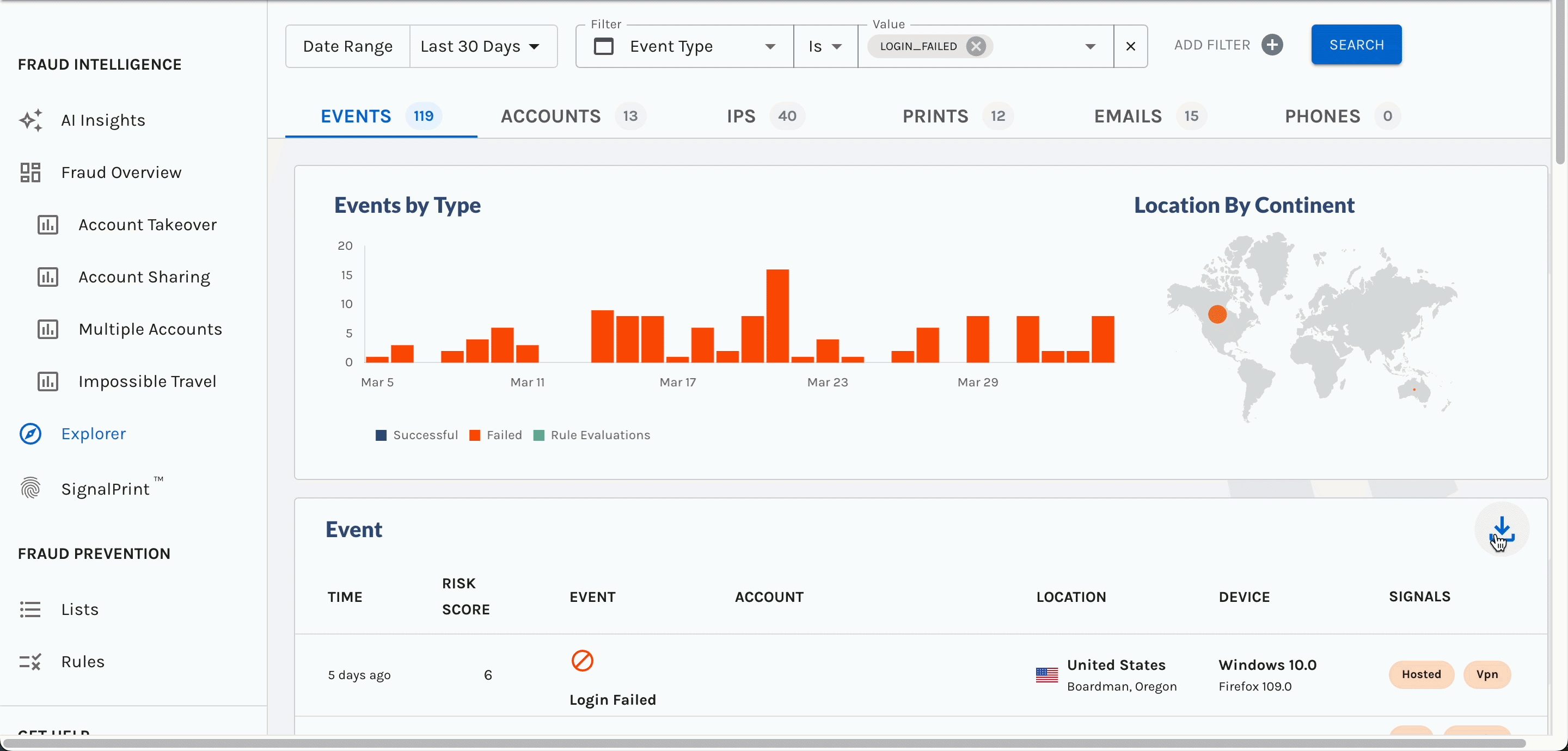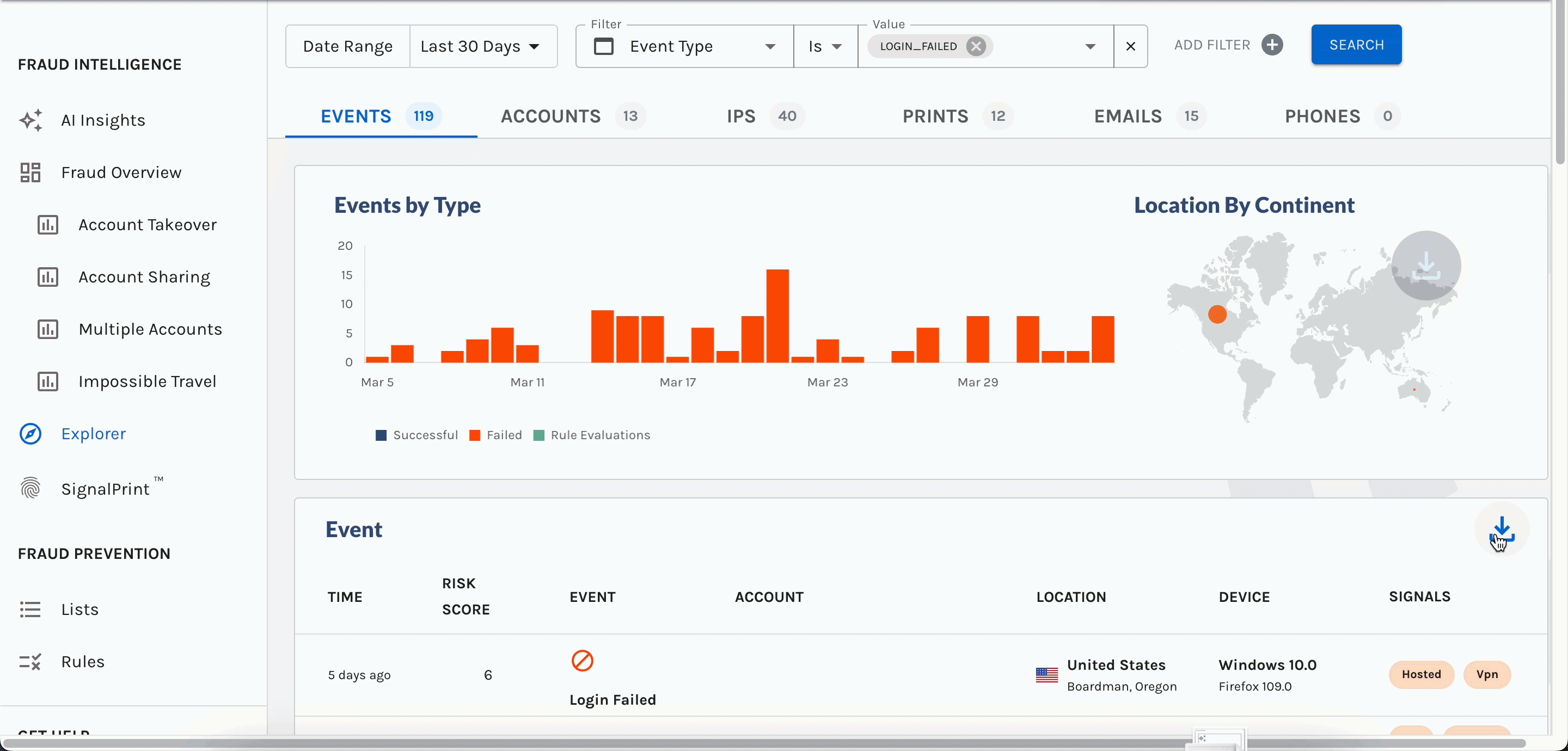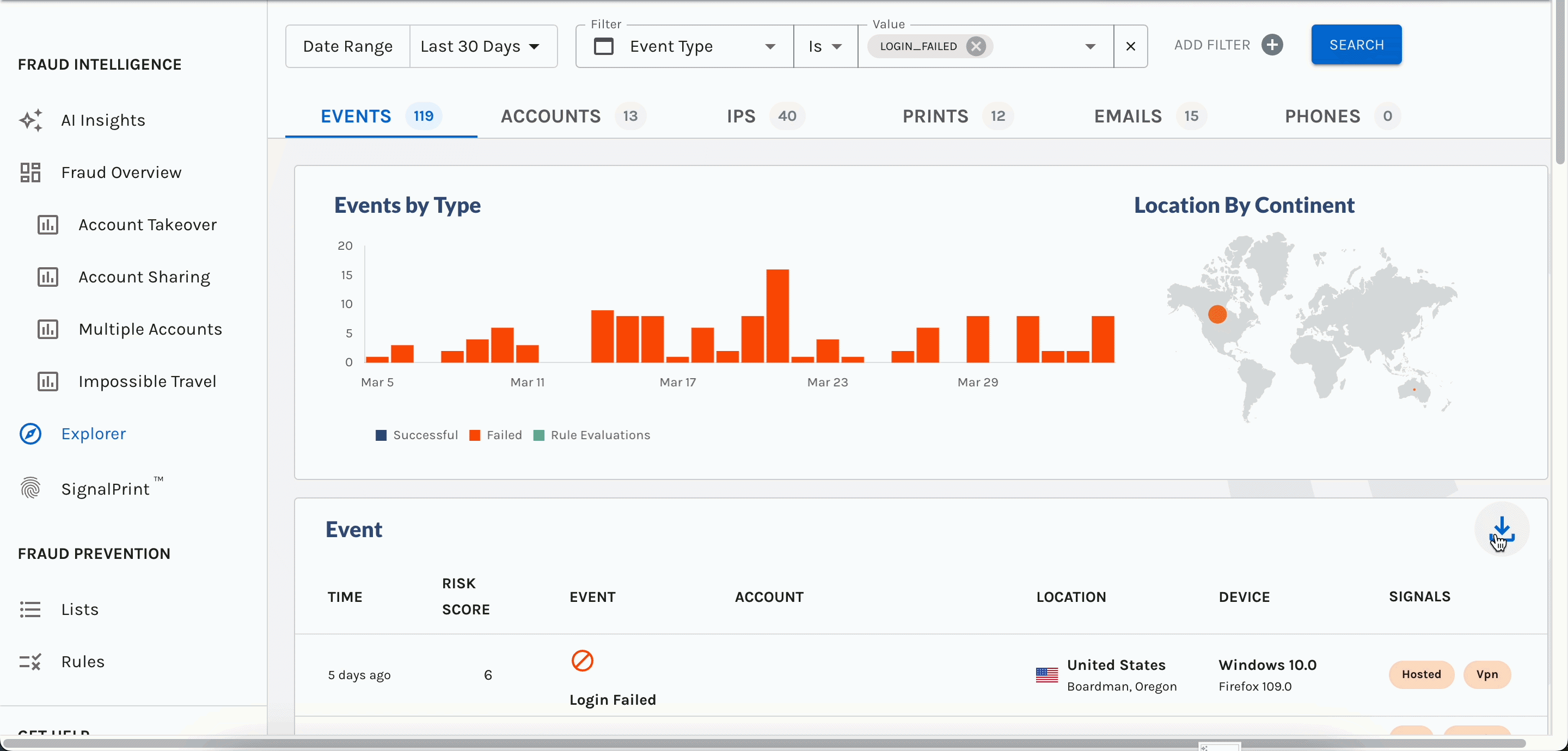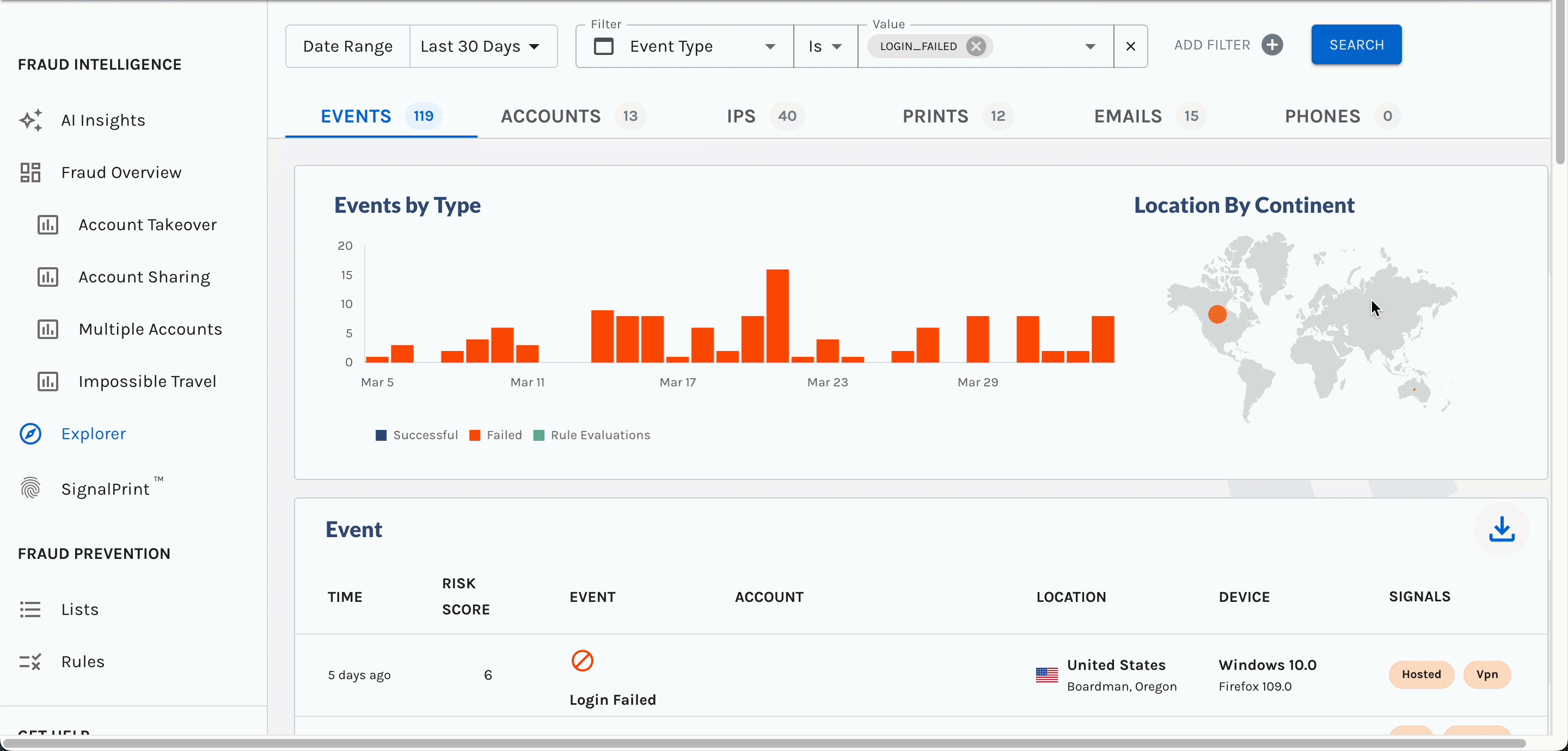
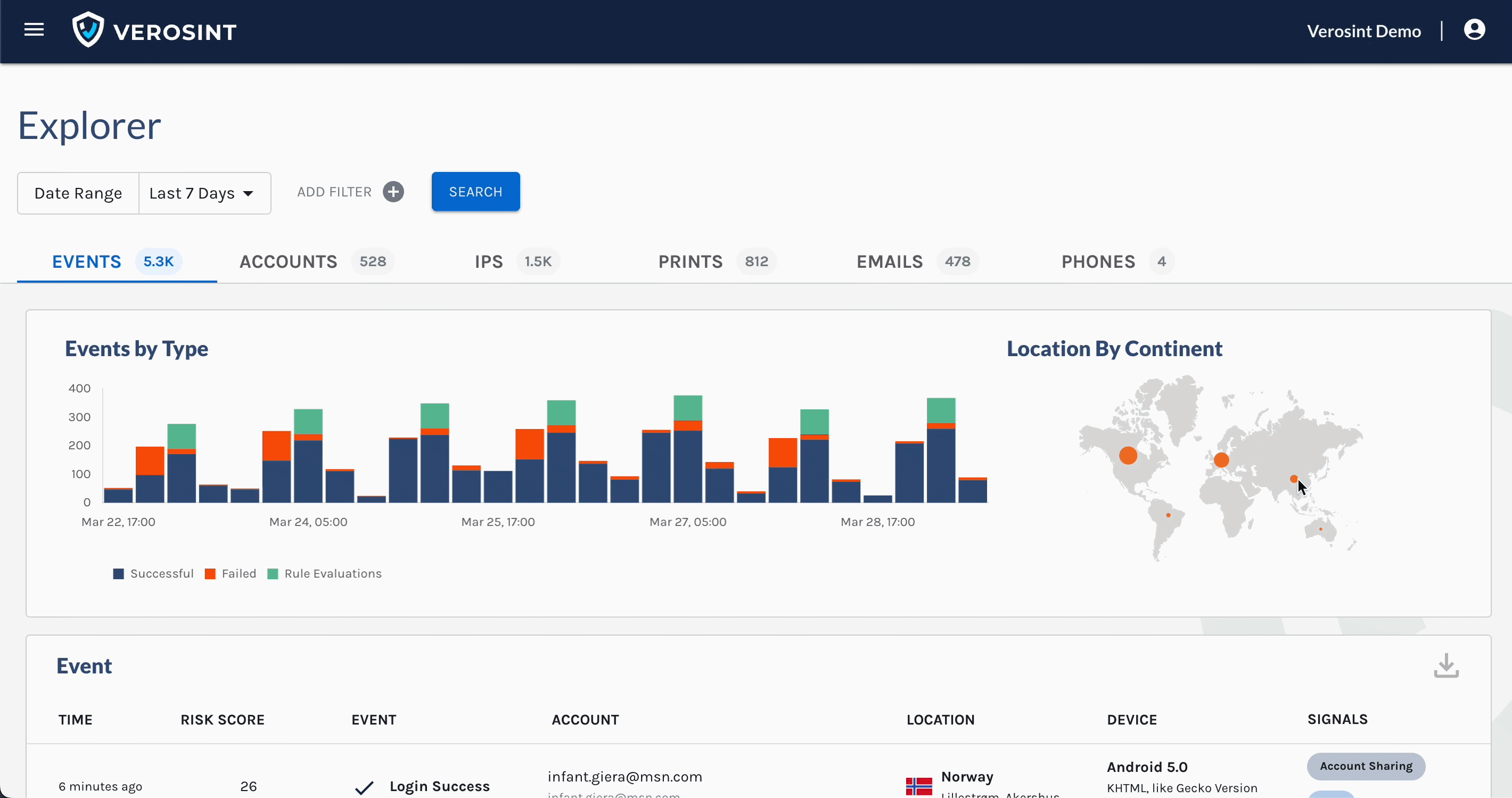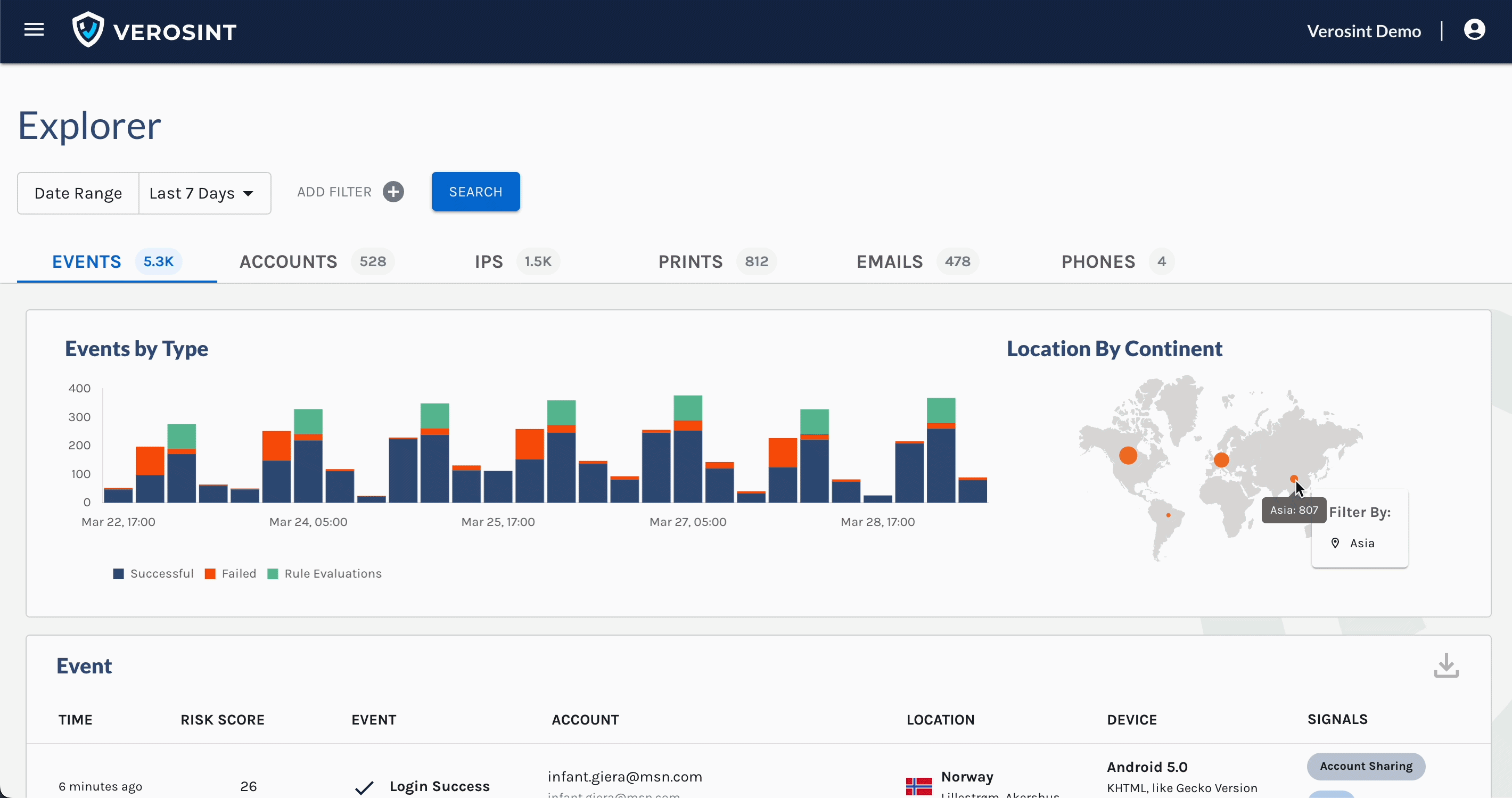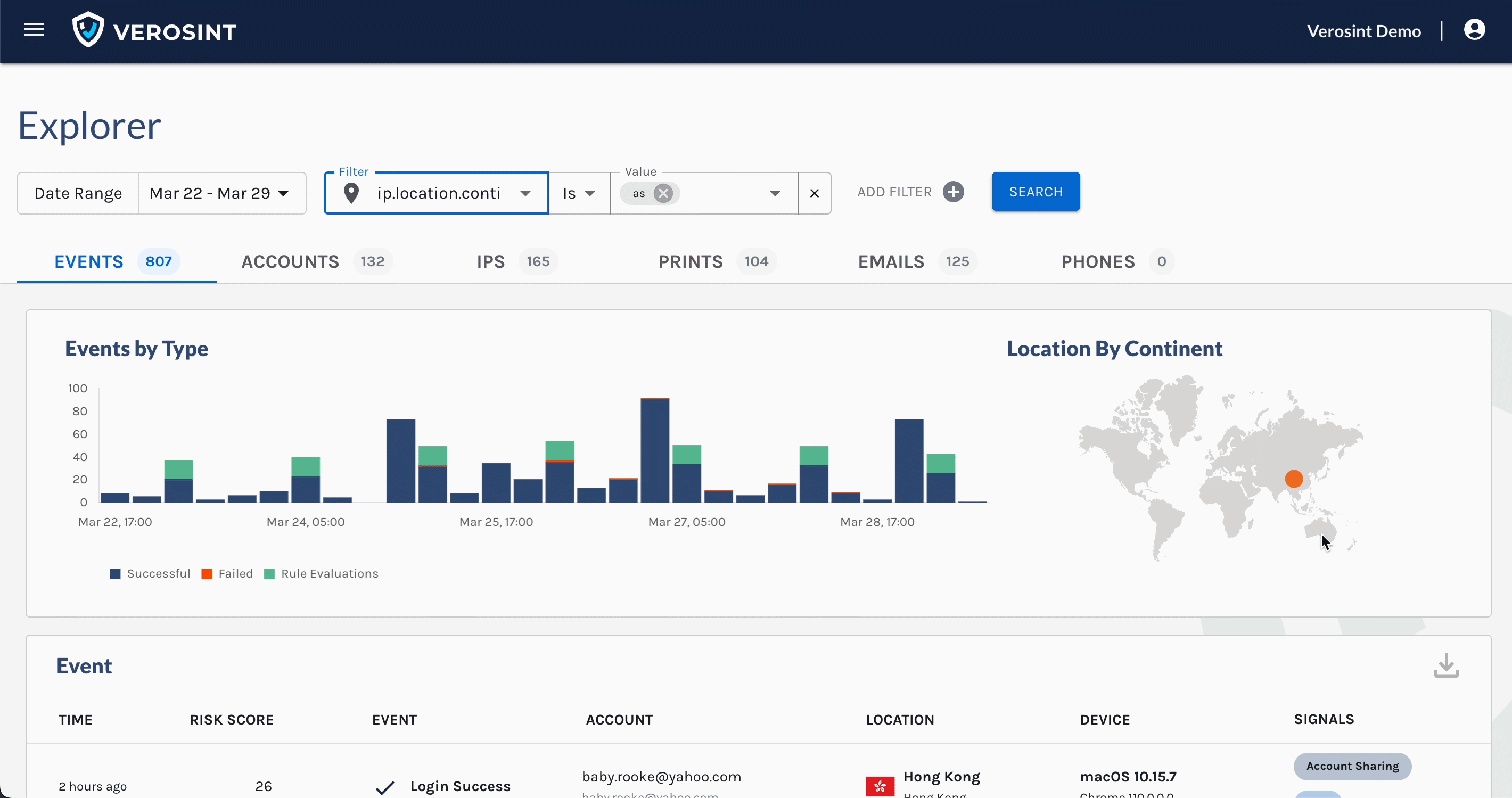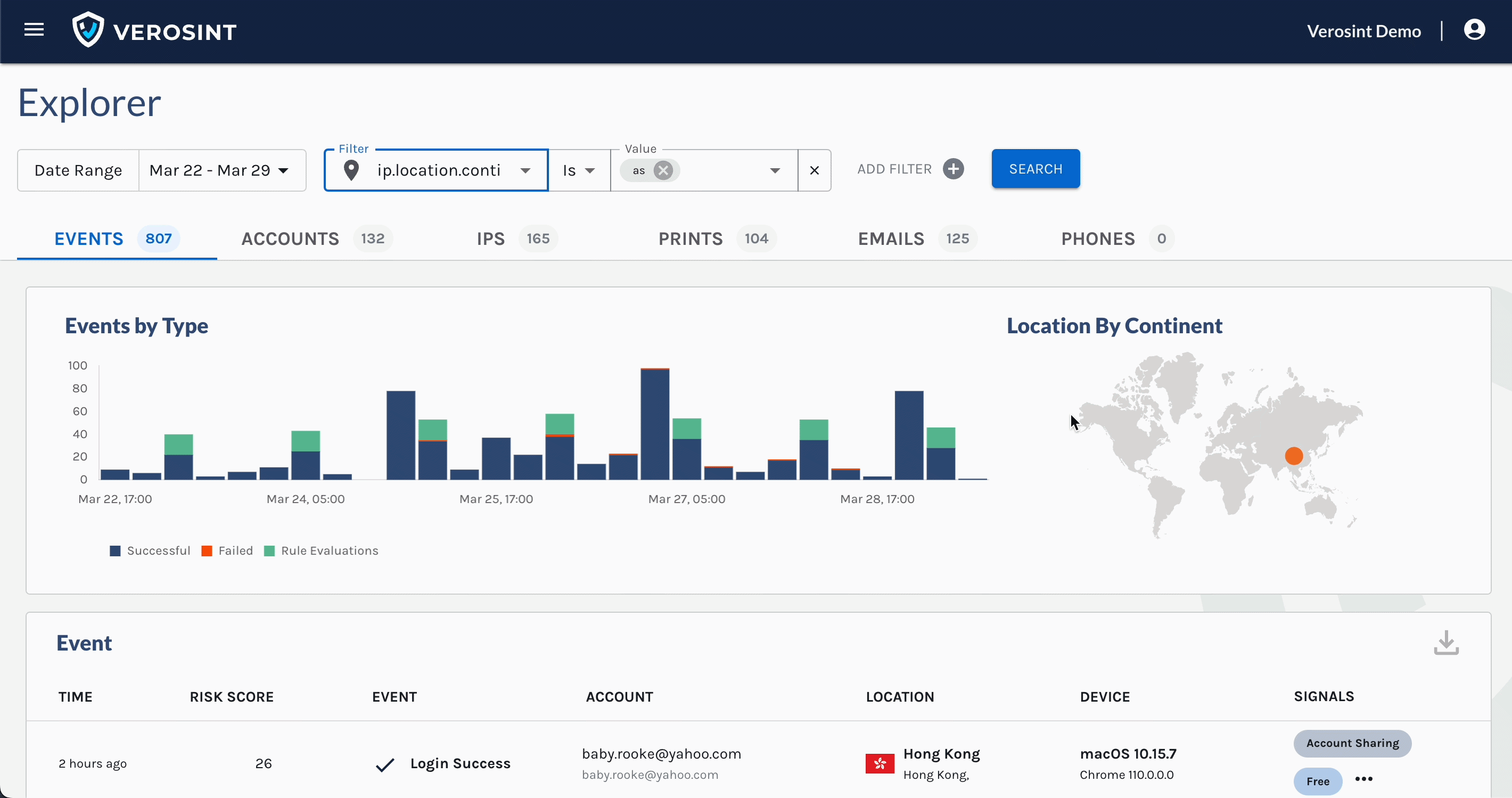
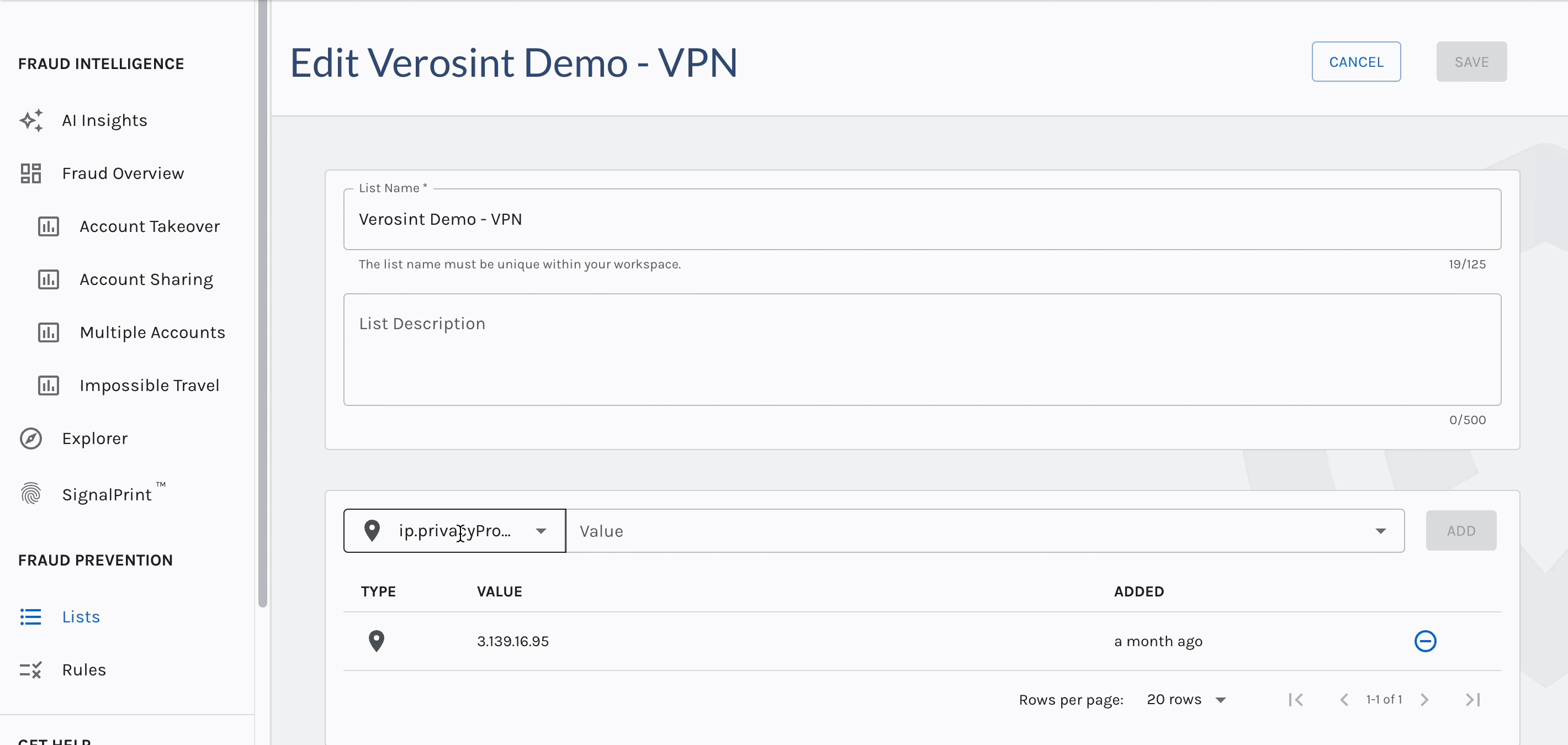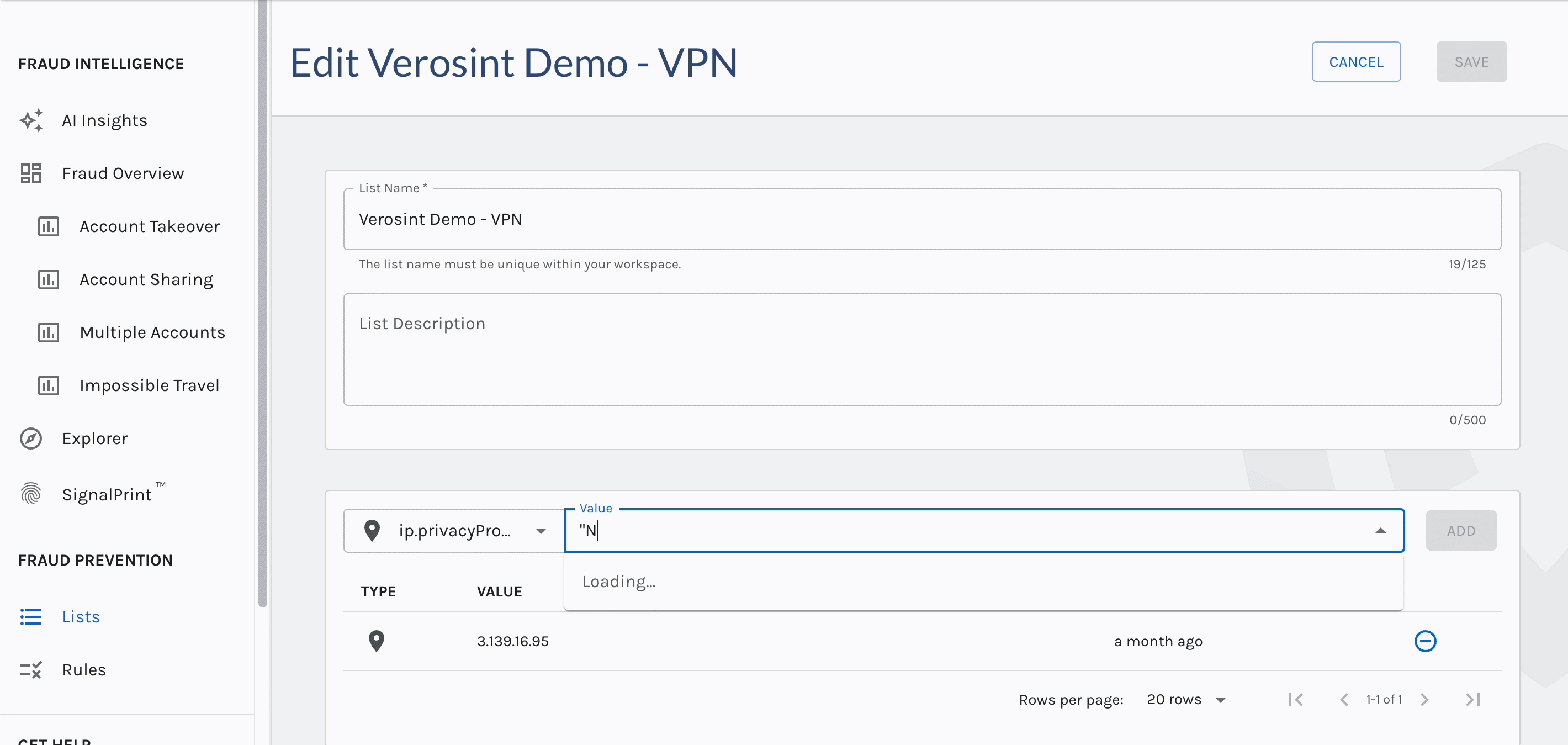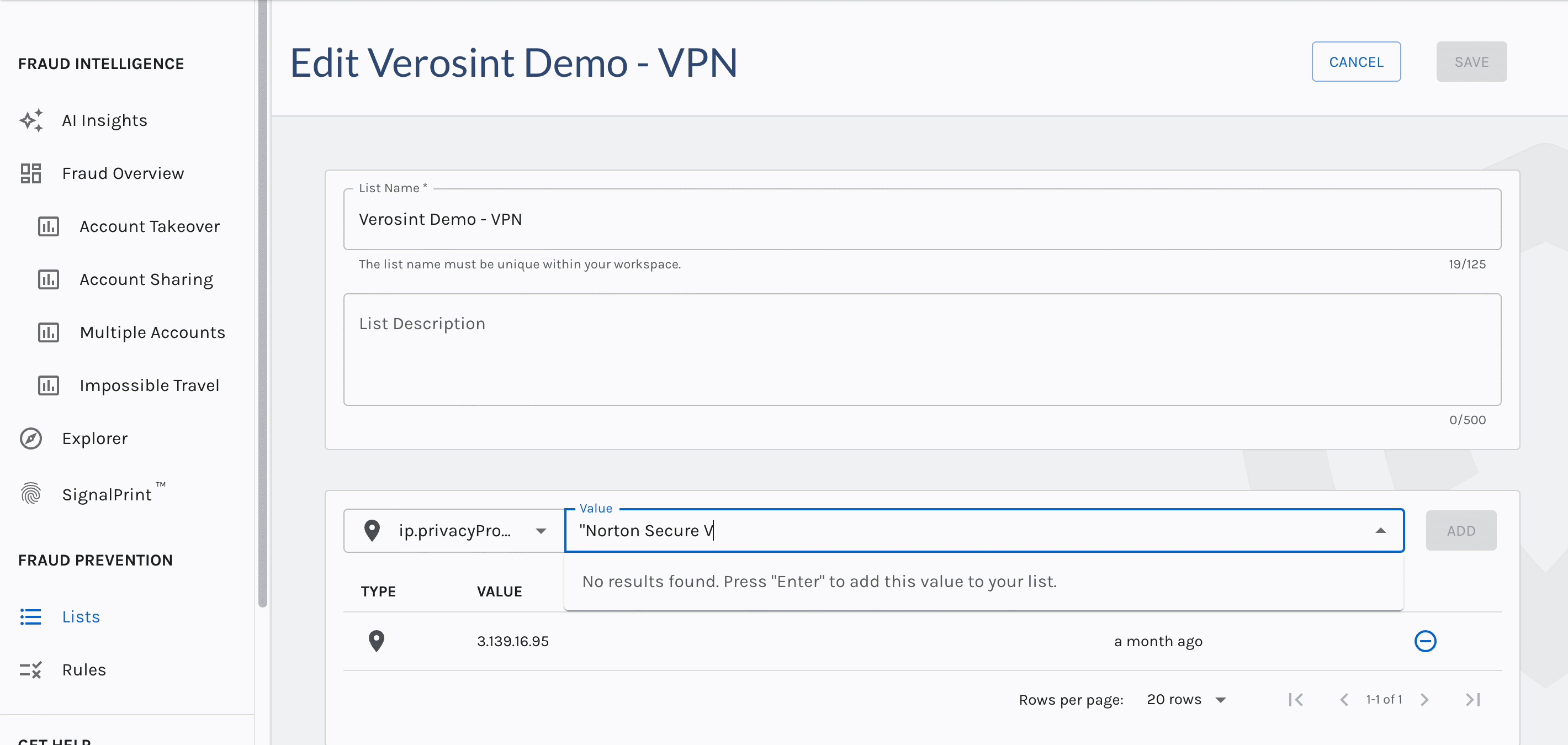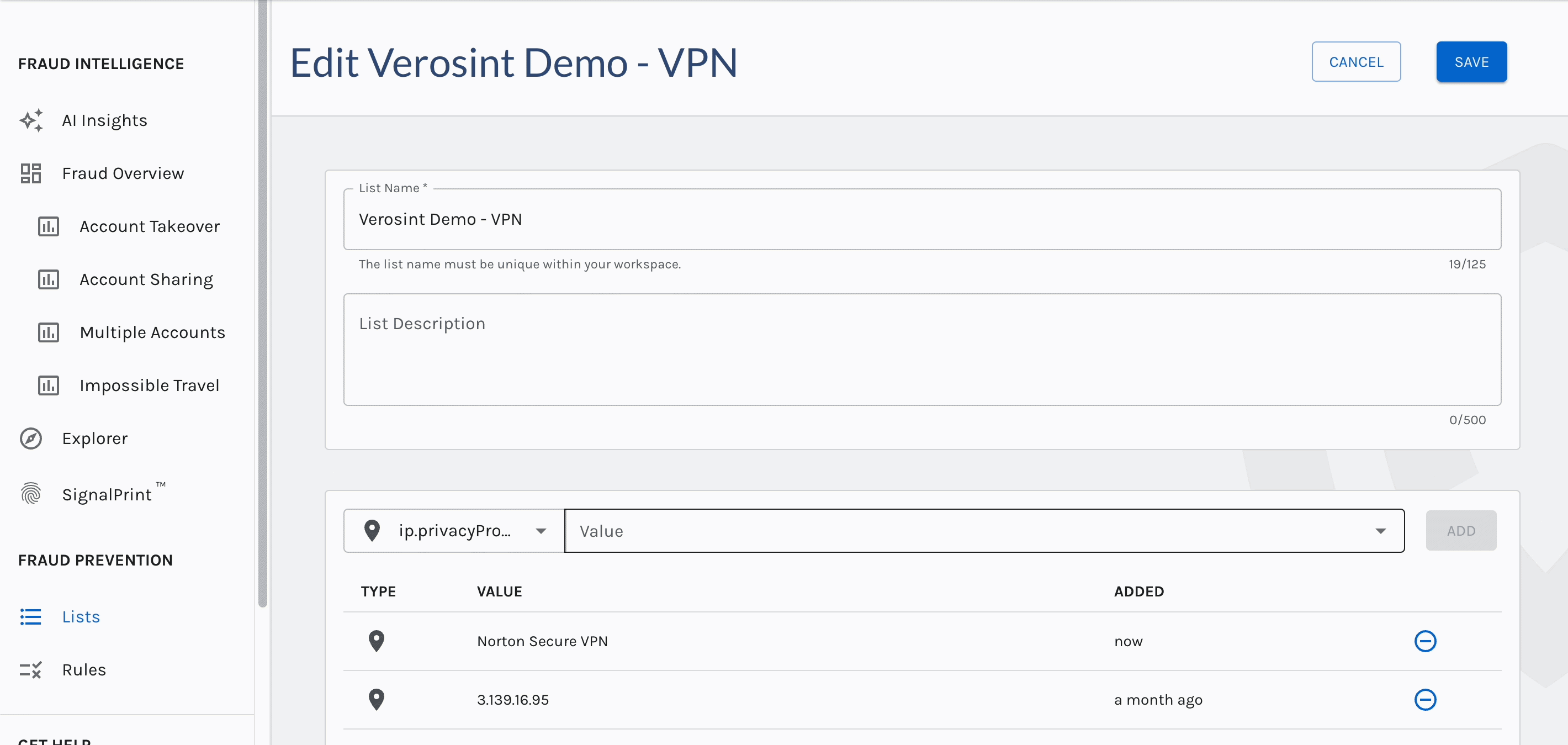
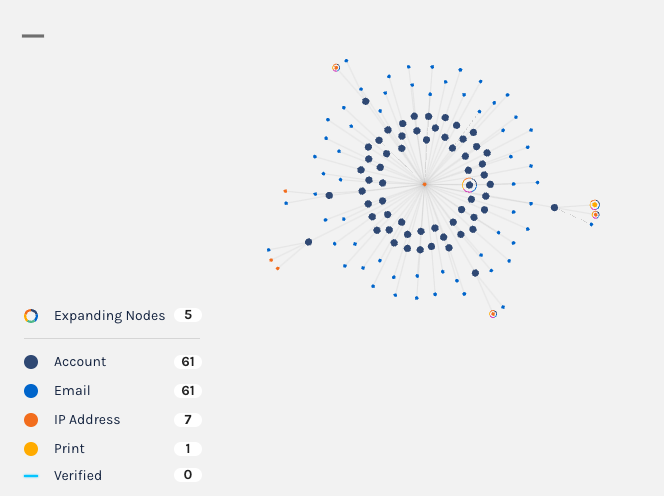
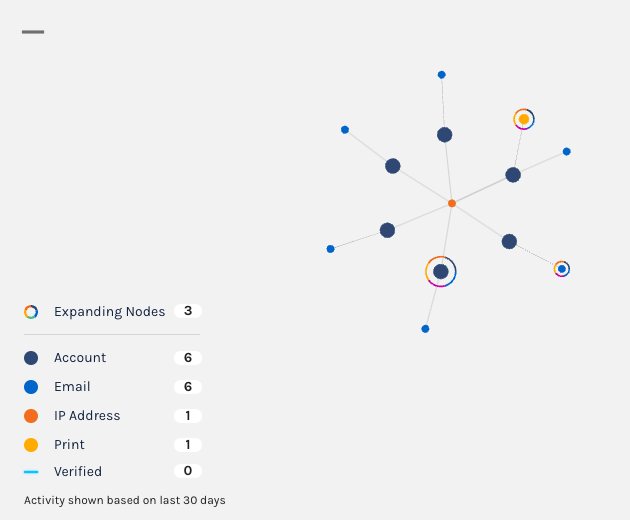
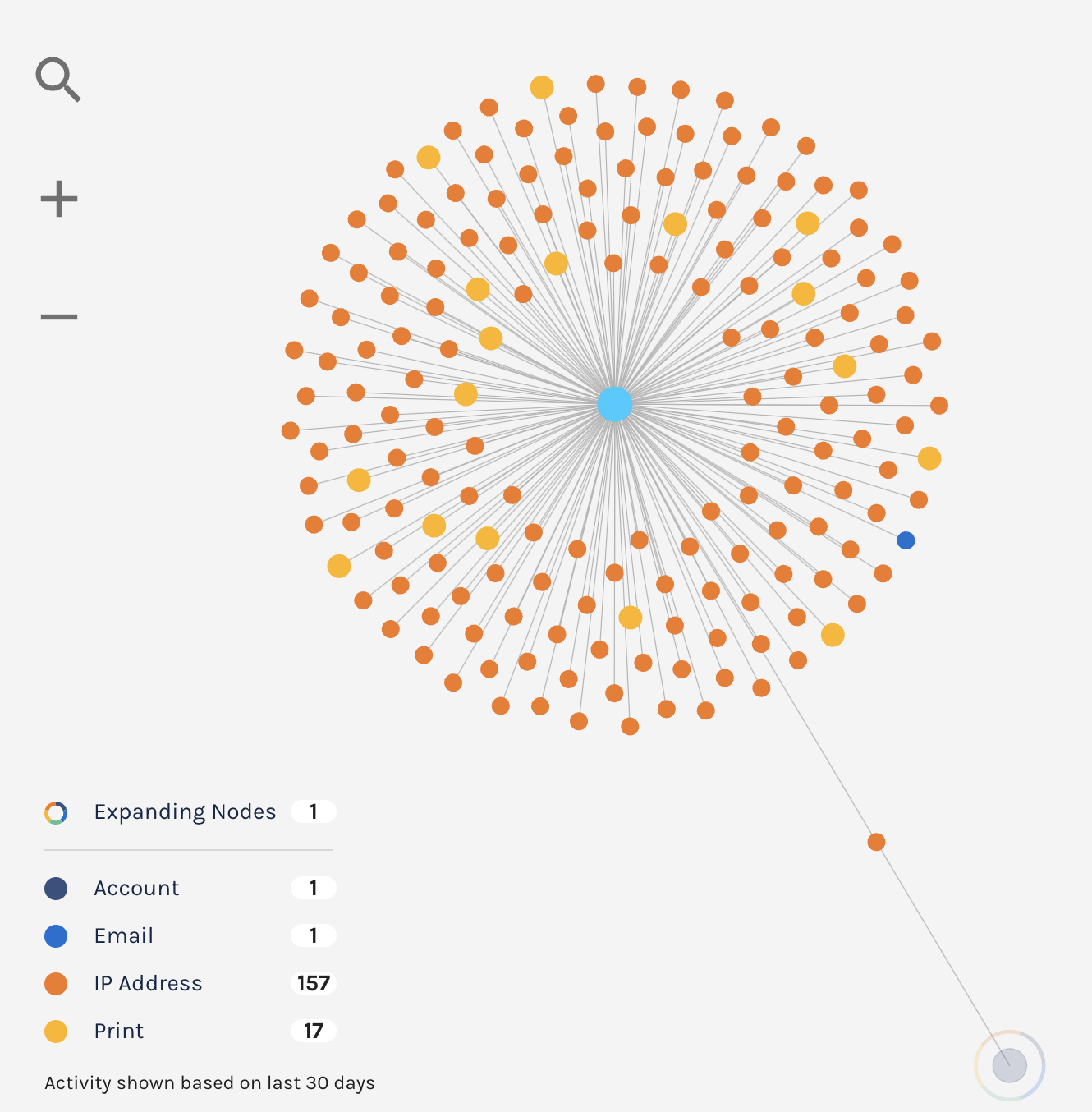
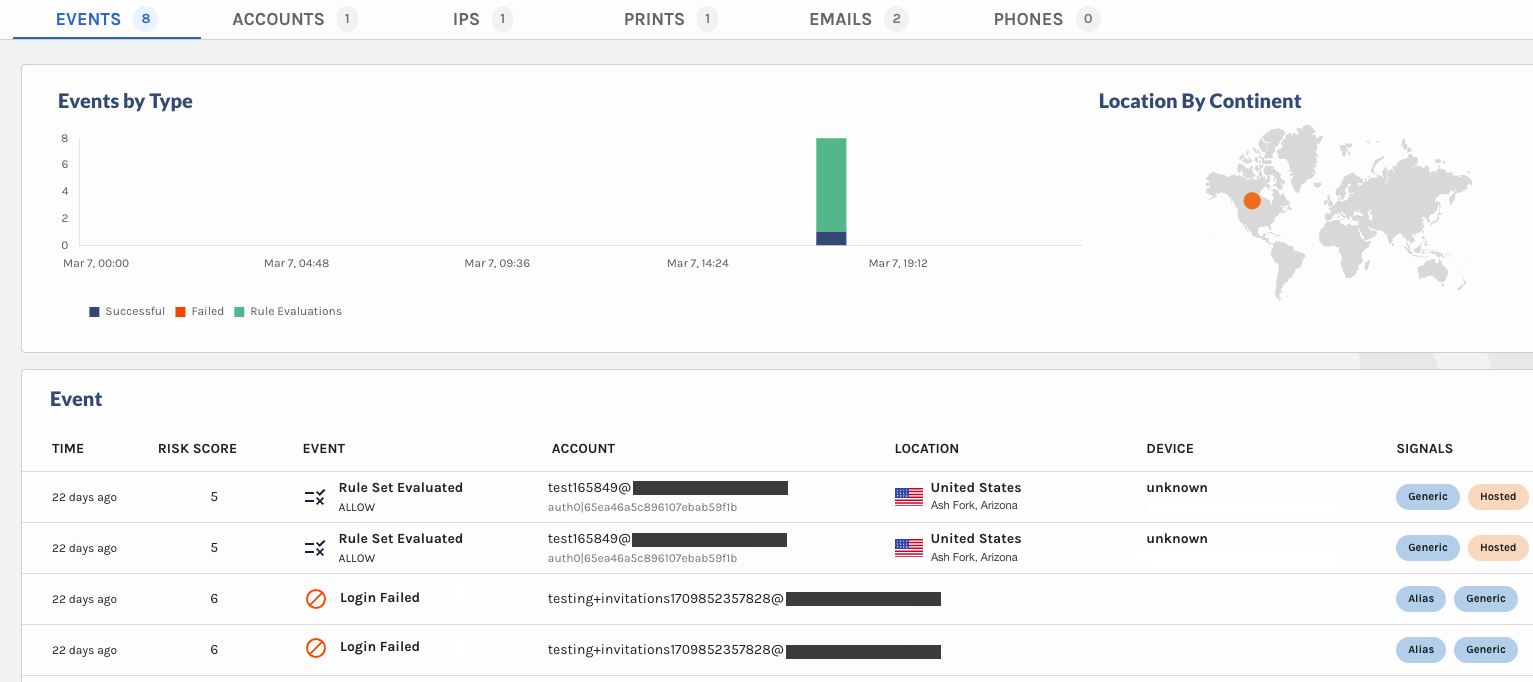
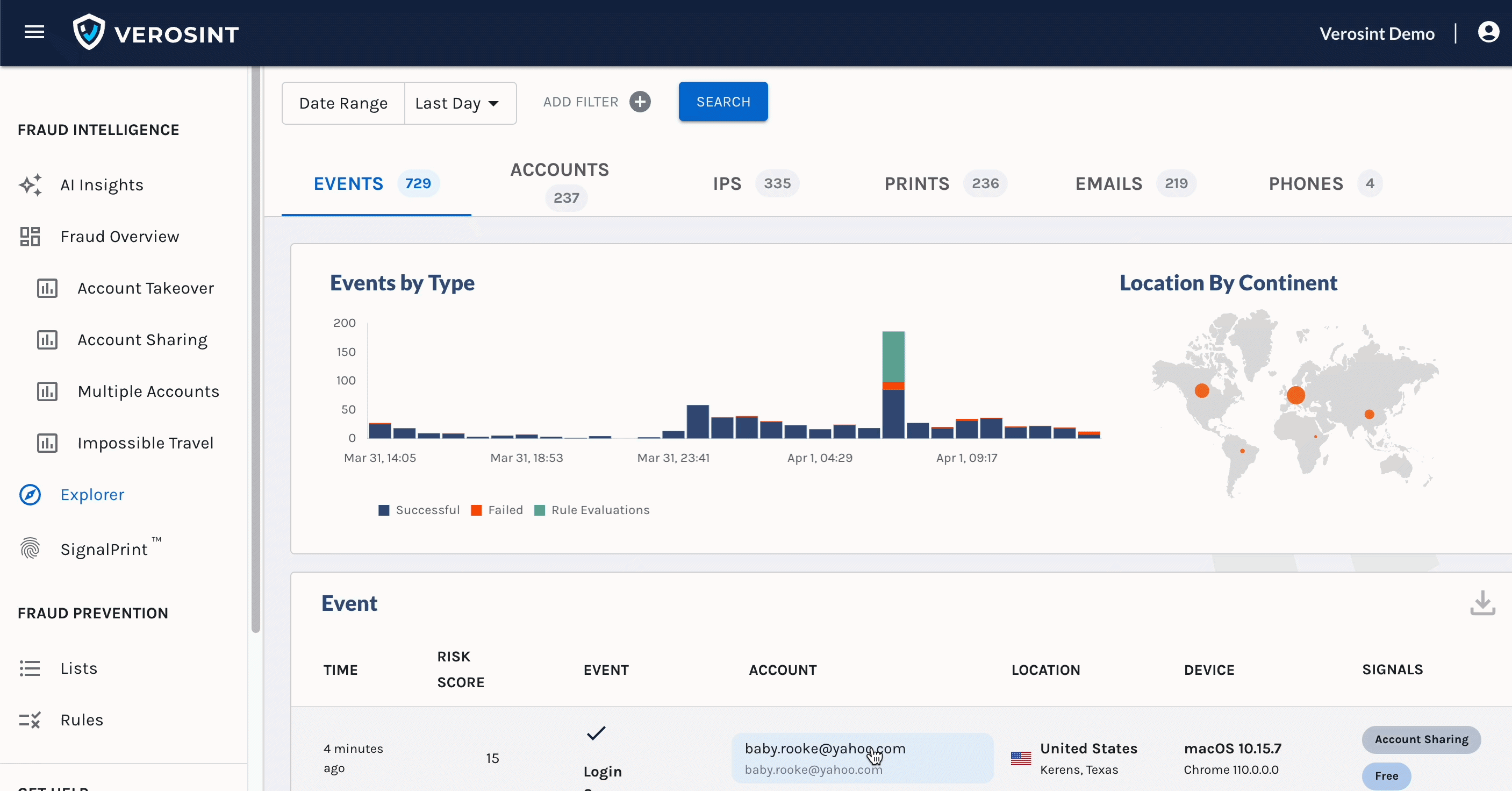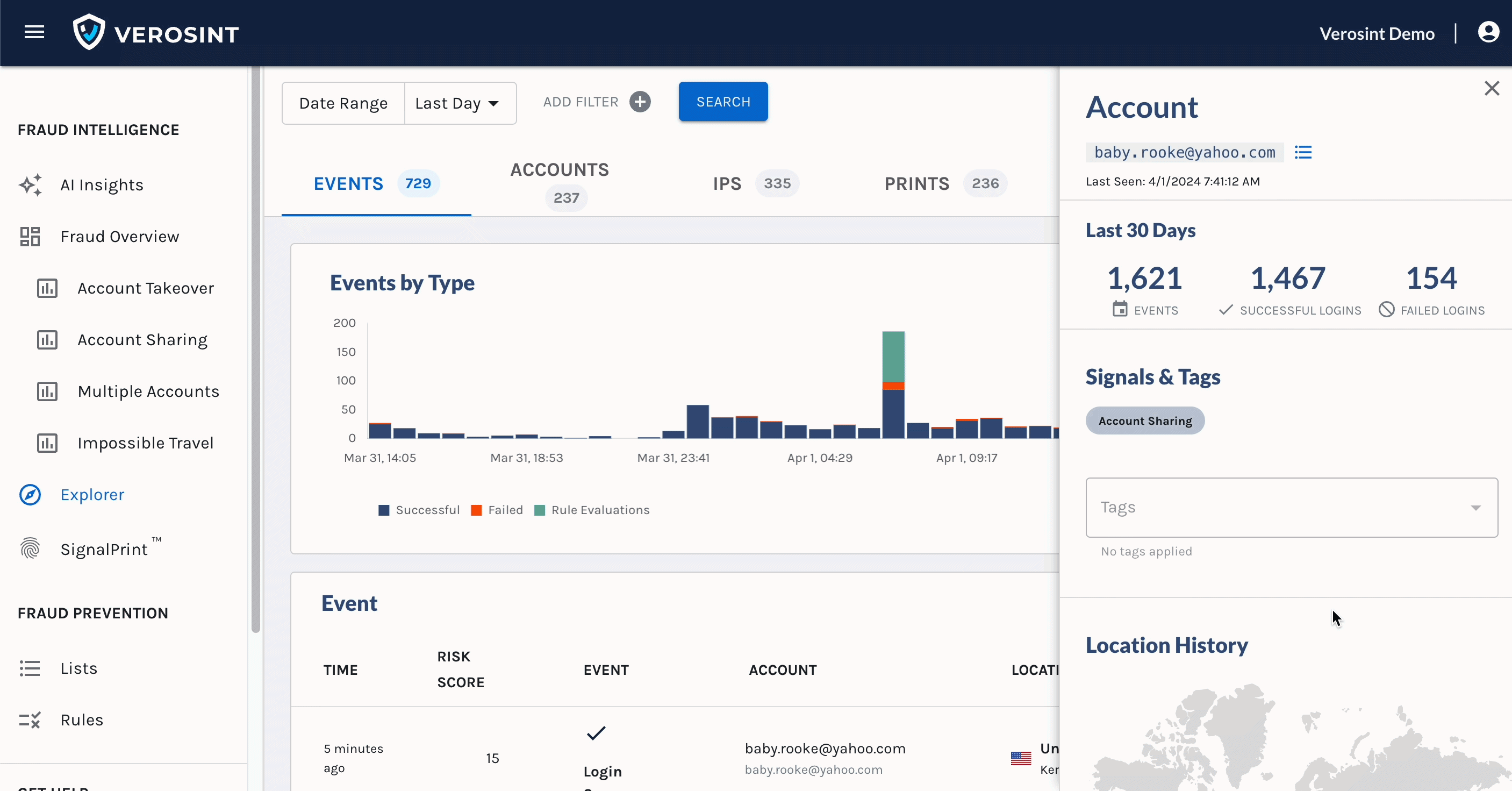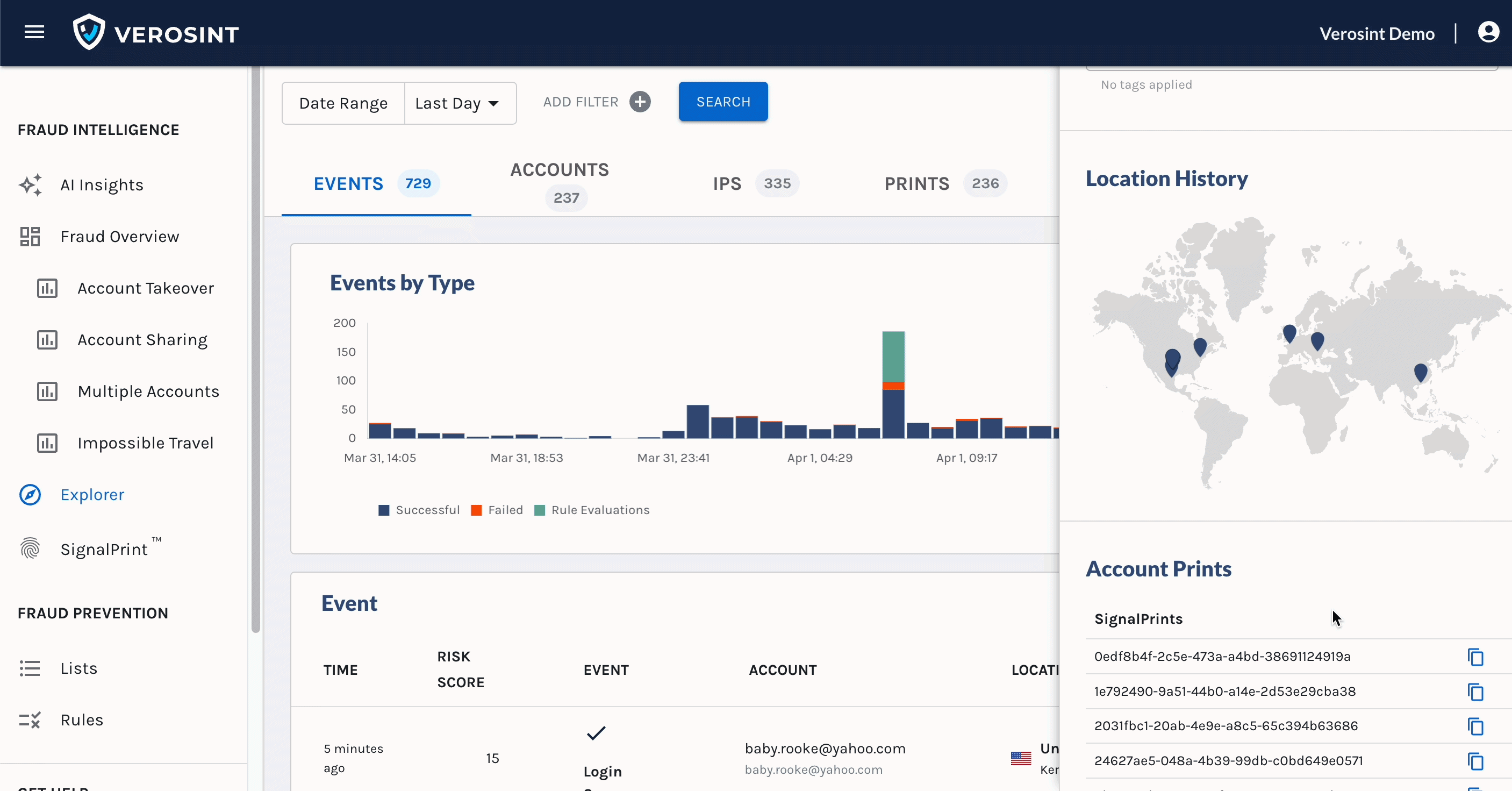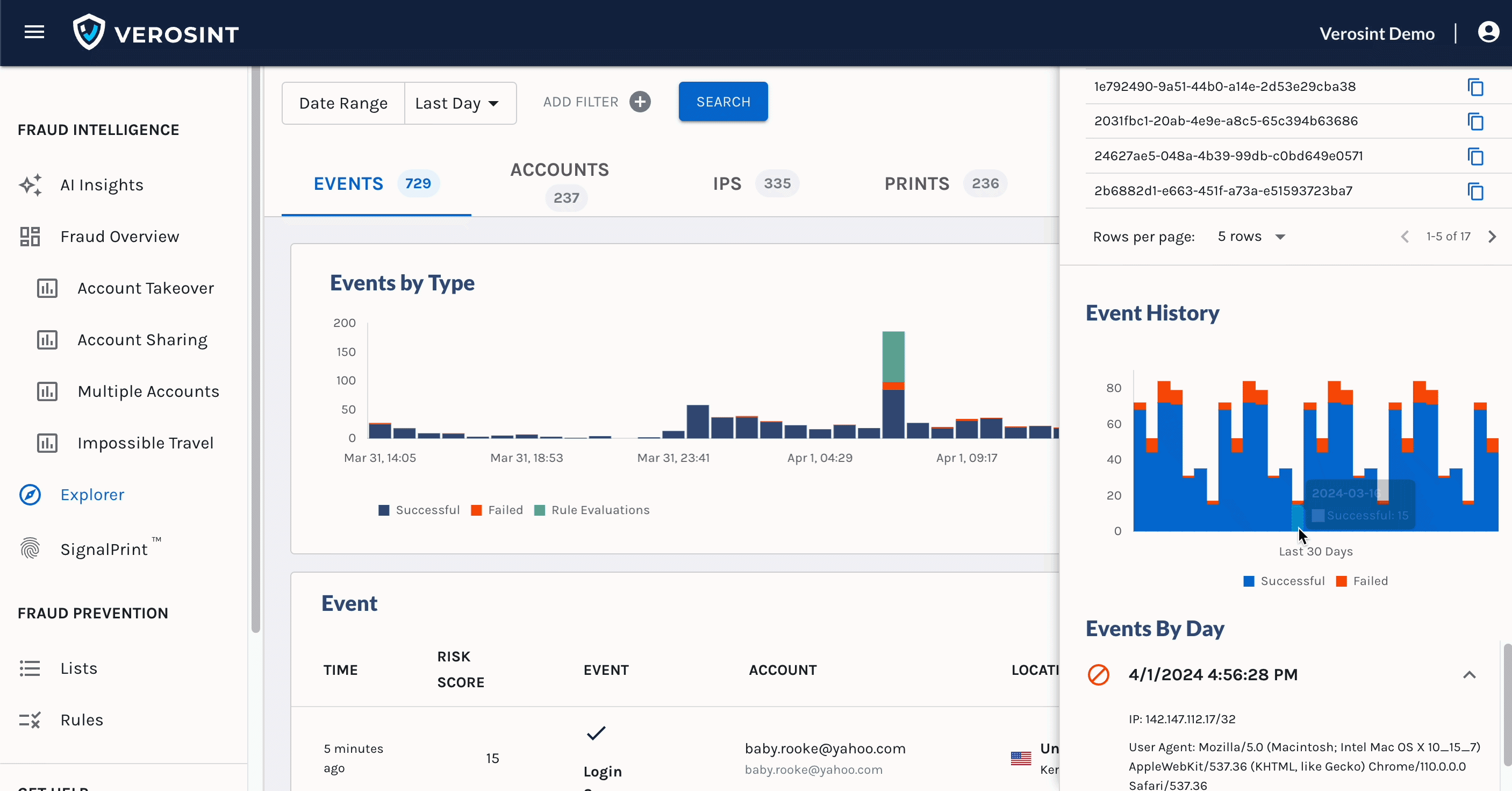
You can now search for
emptyAccount IDs in Explorer, making it easier for you to discover when a potential stuffing attack or account takeover attempt may be occurring.For example, a bad actor may attempt to log into your platform by trying a bunch of email usernames and passwords. If that email username does not exist in your platform, the Account ID will be
emptywhen you search for it in Explorer.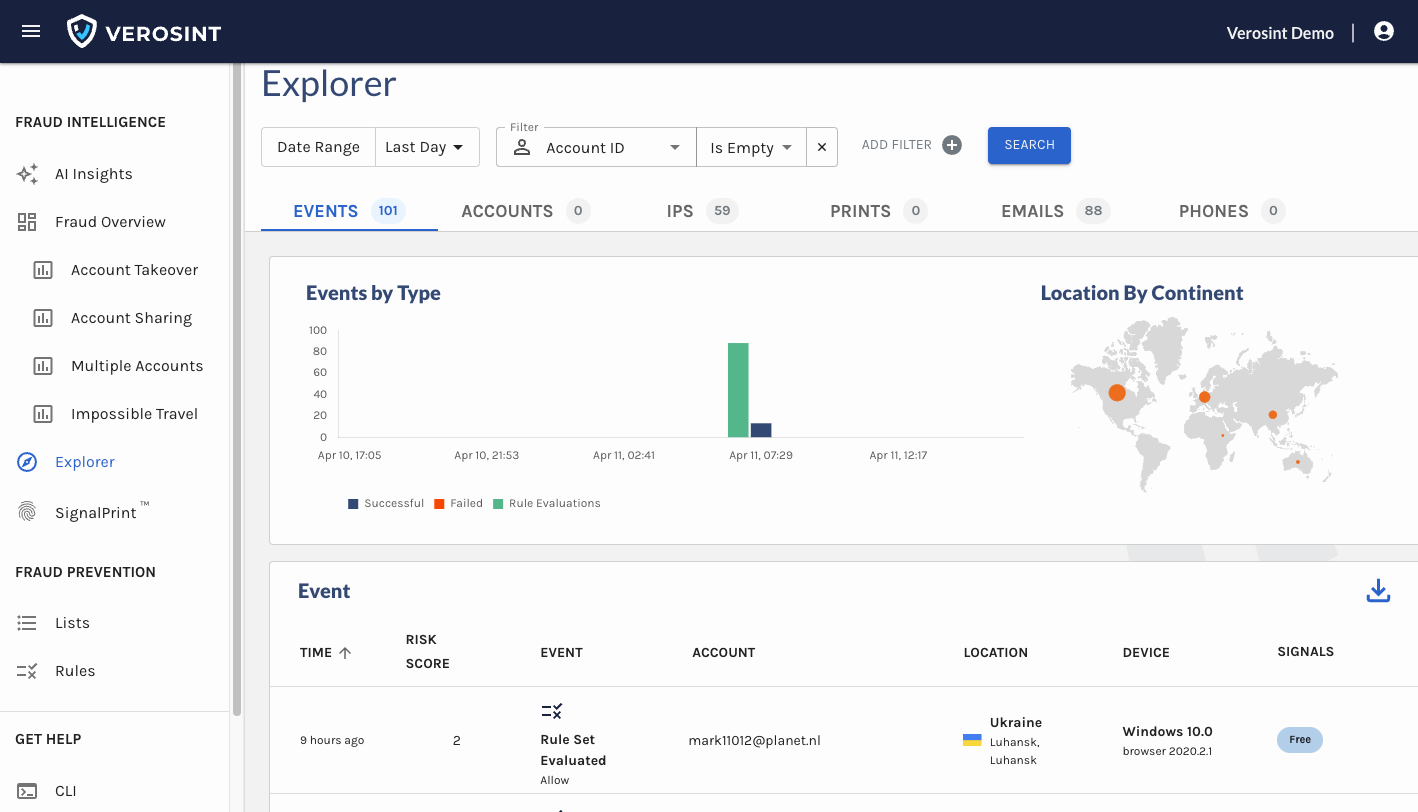
Notice the Account cell contains an Email, but no Account ID